Win10 UWP Calculator
Goals:
- Make the win10 UWP calculator 1+1=3
- Reverse engineering the win10 UWP calculator, understand all (at least most) functionalities.
What is UWP?
Universal Windows Platform (UWP) is a computing platform created by Microsoft and first introduced in Windows 10. The purpose of this platform is to help develop universal apps that run on Windows 10, Windows 10 Mobile, Windows 11, Xbox One, Xbox Series X/S and HoloLens without the need to be rewritten for each. It supports Windows app development using C++, C#, VB.NET, and XAML. The API is implemented in C++, and supported in C++, VB.NET, C#, F# and JavaScript.[1] Designed as an extension to the Windows Runtime (WinRT) platform first introduced in Windows Server 2012 and Windows 8, UWP allows developers to create apps that will potentially run on multiple types of devices. (From Wikipedia)
UWP application usually installed under the directory of C:\Program Files\windowsapp. Usually, users, even administrator, don’t have the permission of editing the files under that directory.
Dynamic Analysis Based on Data Flow
Anchor in the memory
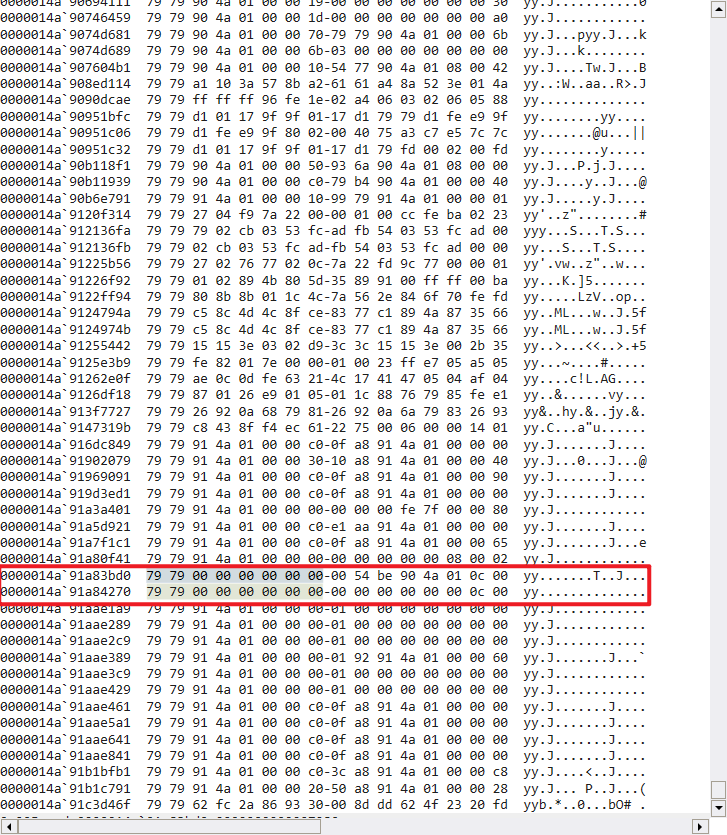
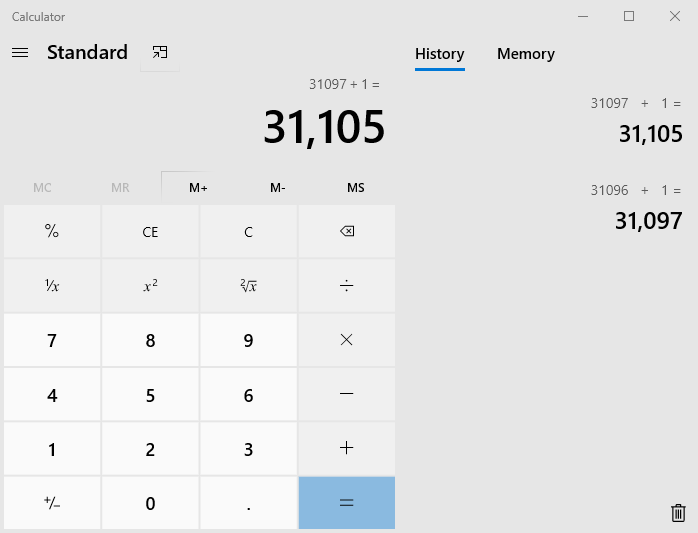
Set the calculation result to a wired number, suppose they are store in somewhere in the memory in hex format (experience from win32 calc), break the program by windbg and search through the memory to see where it is. The result might be complicate, but after identified some key characteristics of the data, only a few of them “might” be the correct value we want. Here I use “yy” in ascii form and 31097 for decimal value to test the memory.
1 | s -a 0 L?fffffffffff "yy" |
Then, assign them with different value in the memory and continue run the calculator. Base on different value we assigned to them, we can easily identify which memory location is the real one. 31097 + 1 will never results 31105, therefore, we found the correct memory location.
1 | ed 0000014a`91a83bd0 0000000000007980 |
Who touches my anchor?
Set up breakpoint on that memory location when any code read it.
1 | ba r 2 0000014a`91a83bd0 |
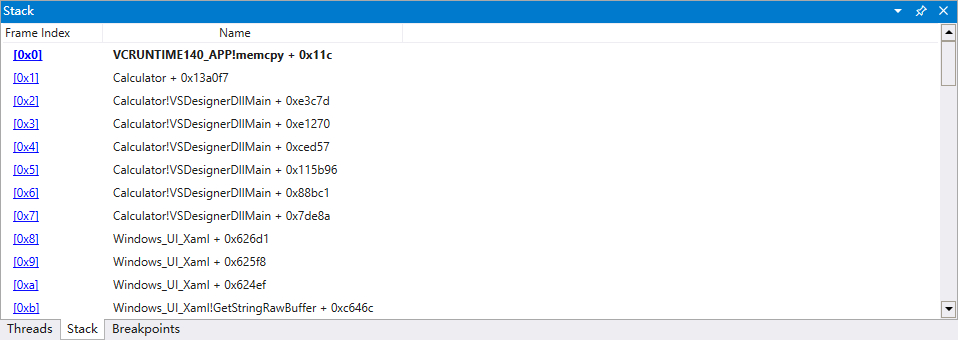
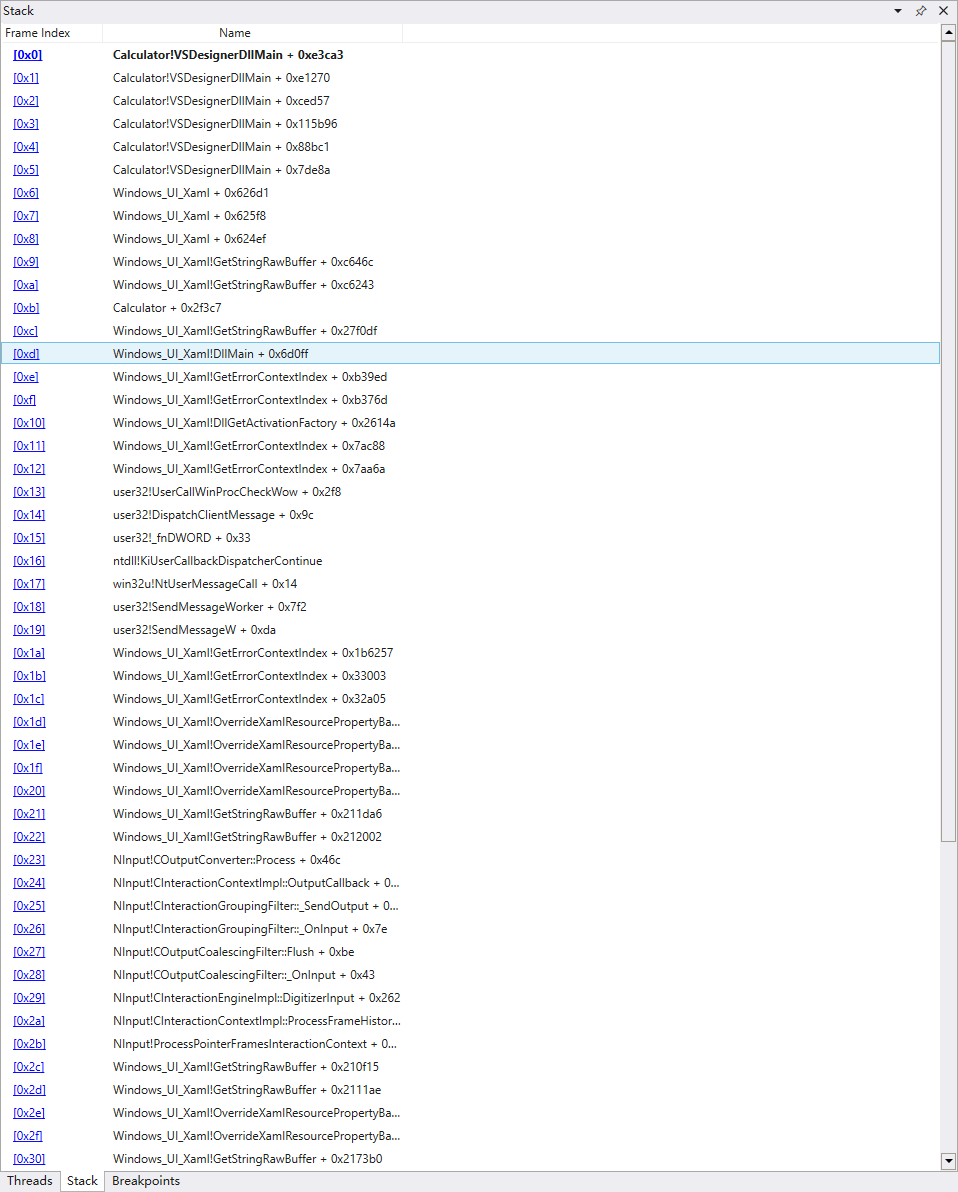
Then when the calculator is running and hitting the “+” button, the program hit the break point with stack organization (also the control flow) shown as below.
The current function call is in the library(like “printf” function for c code in stdio.h), ignore that. Step out the current function and examine the code.
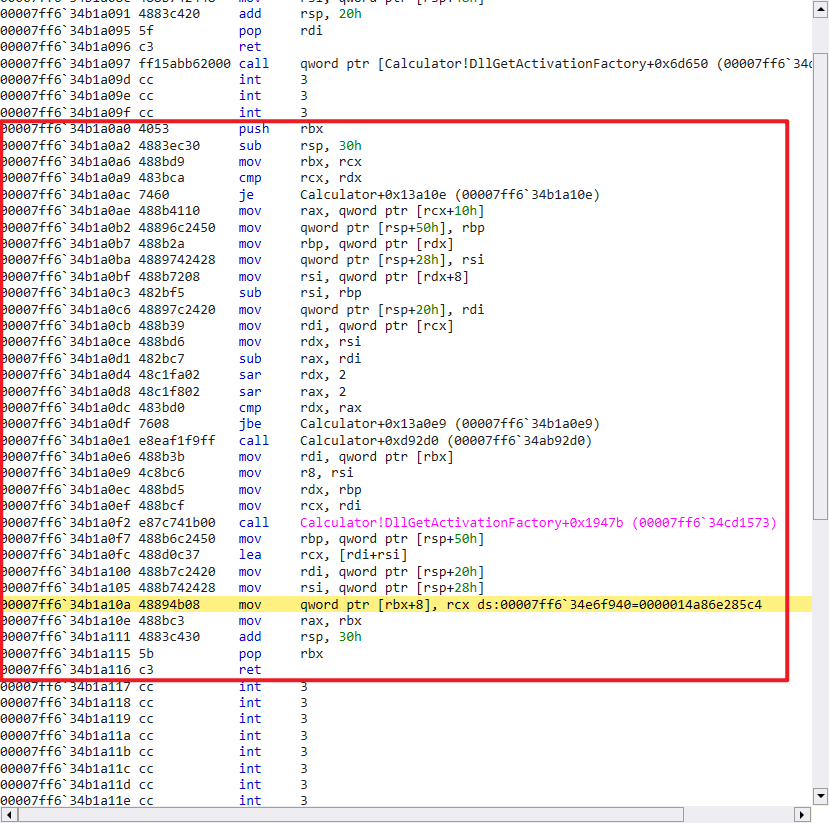
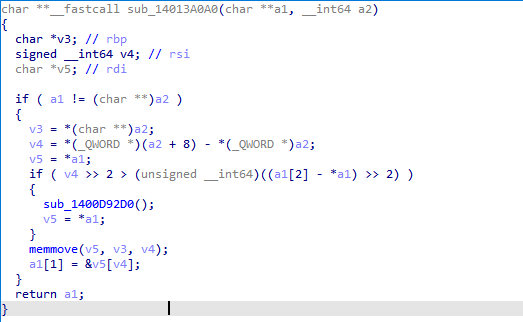
Locate it in the IDA, combine the dynamic analysis stack contents, the **a1 is a double pointer of one of the number we want to add. We guess that **a2 could be another double pointer which points to the number we want to add (Not add yet, this breakpoint happened just after we push the button “+”)
The whole control flow is shown in the below:
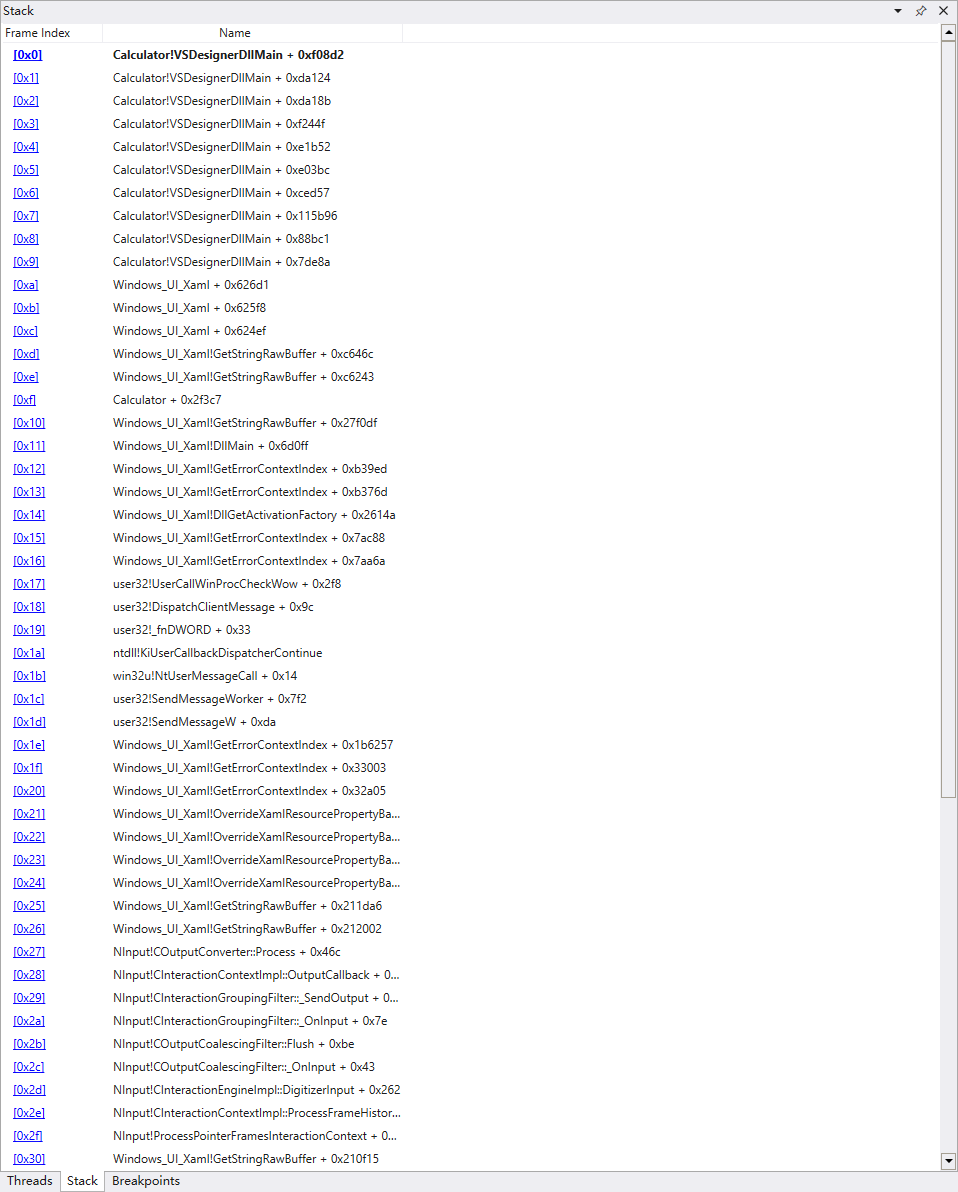
After figure out the control flow of the “+” button, another button will also cause the break point, “=” button. Using same idea, drag out the control flow of the “=” button.
It is worth noting that this function manipulates both input we use to add the number.
It get called under this function.
Until now, we have discovered a lot about the “+” and “=” buttons, let’s move on to the static analysis part.
Static Analysis
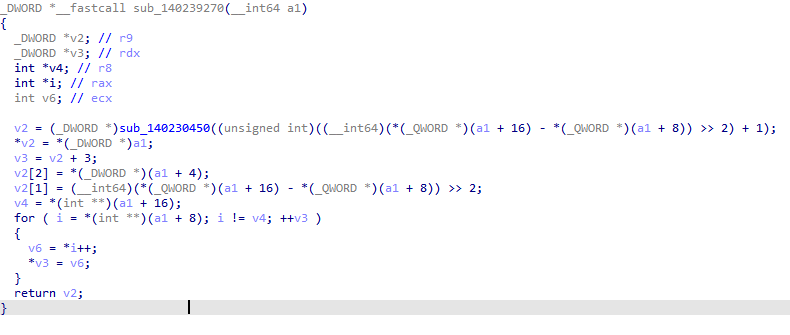
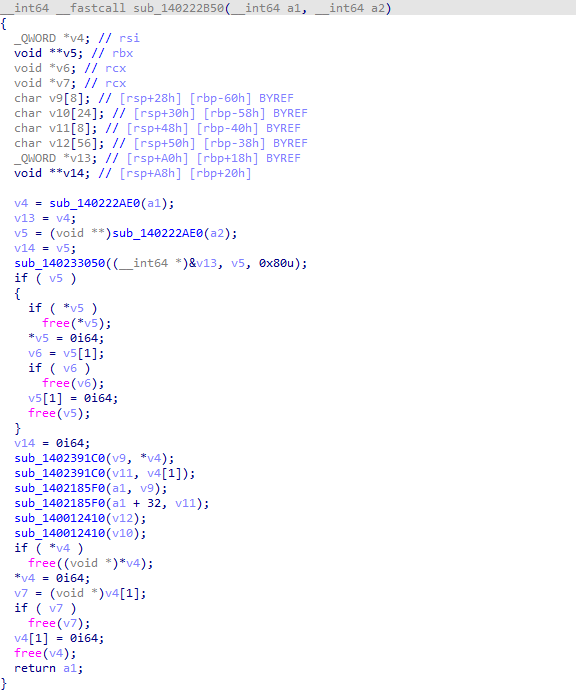
Two important functions are: sub_140239270 and sub_140222AE0 do not have any sign to do the addition. Rather, sub_140239270 place space for both numbers we want to add. sub_140222AE0 returns an array with both pointers pointing to the numbers we want to add.
So the addition will appear in higher level functions.
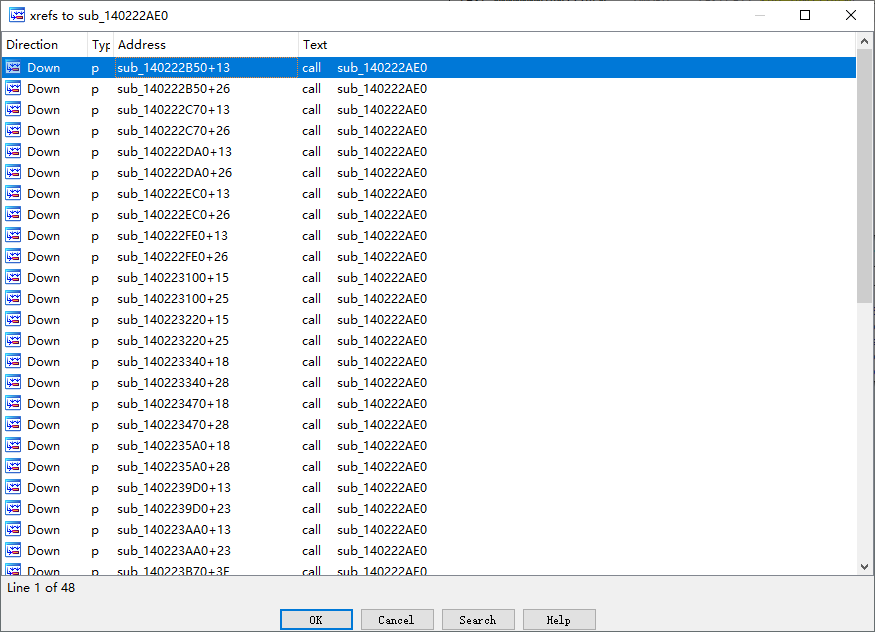
What’s more, sub_140222AE0 was found always to be called in pairs. It is reasonable to speculate that other functions are likely to be other operators (addition, subtraction, multiplication, division, …, etc)
The caller function of sub_140222AE0.
Just after two sub_140222AE0 function calls, sub_140233050 do the addition. It updates the pointer in the v13, which stores the new value after the addition. With this information, the challenge will be solved soon.
Hook
Originally will use frida to hook the function, but it has some bug when attach to the UWP calculator. So I decide to use windbg scripting instead.
After search for the windbg scripting, the search results shows that windbg can be script using JavaScript files.
1 | dx Debugger.State.Scripts.EXP.Contents.EXP(2) |
1 | ; |
Achievement display
Thanks
Atum
Tencent Spark Program
References
UWP逆向初接触 | l1nk3dHouse (showlinkroom.me)
(1/2) 为了理解 UWP 的启动流程,我从零开始创建了一个 UWP 程序 - walterlv
(2/2) 为了理解 UWP 的启动流程,我从零开始创建了一个 UWP 程序 - walterlv
Universal Windows Platform - Wikipedia
GDB commands for WinDbg users | Matthew Justice’s blog (mattjustice.com)
Common WinDbg Commands (Thematically Grouped)
s (Search Memory) - Windows drivers | Microsoft Docs
ba (Break on Access) - Windows drivers | Microsoft Docs
e, ea, eb, ed, eD, ef, ep, eq, eu, ew, eza (Enter Values) - Windows drivers | Microsoft Docs
x64 calling convention | Microsoft Docs
MASM Numbers and Operators - Windows drivers | Microsoft Docs
JavaScript Debugger Scripting - Windows drivers | Microsoft Docs